From WAF to MFA: Critical Recommendations to Secure Digital Transactions

As restaurants and convenience stores increase business on digital channels, hackers are focusing more on these industries to find security gaps and exploit customer information. Hacker activity ranges from placing orders with saved credit cards from compromised accounts (known as "Account Takeovers" or ATOs) and extracting value from gift cards and transferring it to other accounts, to using a brand's login page to test if login information from other data breaches works on other high-value sites.
Brands must ensure they have robust security measures in place to safeguard their digital channels from these attacks and provide customers with peace of mind when they purchase. At Bounteous X Accolite, we are continuously evolving the layers of security that protect our clients' websites and apps, with even more mechanisms being introduced in the next quarter.
First Priority: WAF
Of the security protection layers we recommend to our clients, the first and arguably most important is the Web Application Firewall, or WAF. All incoming requests must pass through this layer before they are handled by the server, and its main goal is to ensure the traffic is from legitimate customers before it is allowed to pass. While there are a number of WAF platforms on the market, we have chosen Cloudflare for a variety of reasons, but primarily because it has a wide array of defense mechanisms that can be deployed and rotated to tackle a variety of incoming attacks.
The methods we typically deploy include:
- Javascript-managed challenges and mTLS to ensure the traffic is coming from a trusted and non-automated source
- Geo-based blocking rules to block traffic coming from areas where our clients' services are not available
- Rate-limiting rules that are constantly being changed to address new attack vectors
- API shield which uses machine learning to analyze and reconfigure rules to rapidly adapt to unexpected attack signatures
At our API Layer, we require traffic to first come through Cloudflare, or we deny the request. If the traffic passes Cloudflare's protection mechanisms, then our NomNom API begins processing the request. With version 5 of the NomNom API, a new "Token of Power" (ToP) eliminates the need for frontend clients to have access to third-party user access tokens, so the first step the API takes is to validate that the ToP is valid before doing further processing. If that succeeds, we use the identity associated with the ToP to ensure the request is scoped to the logged-in user and data for other customers can't be accessed. And finally, our API has logic built in to eliminate "replay attacks" where automations can try an identical request a number of times.
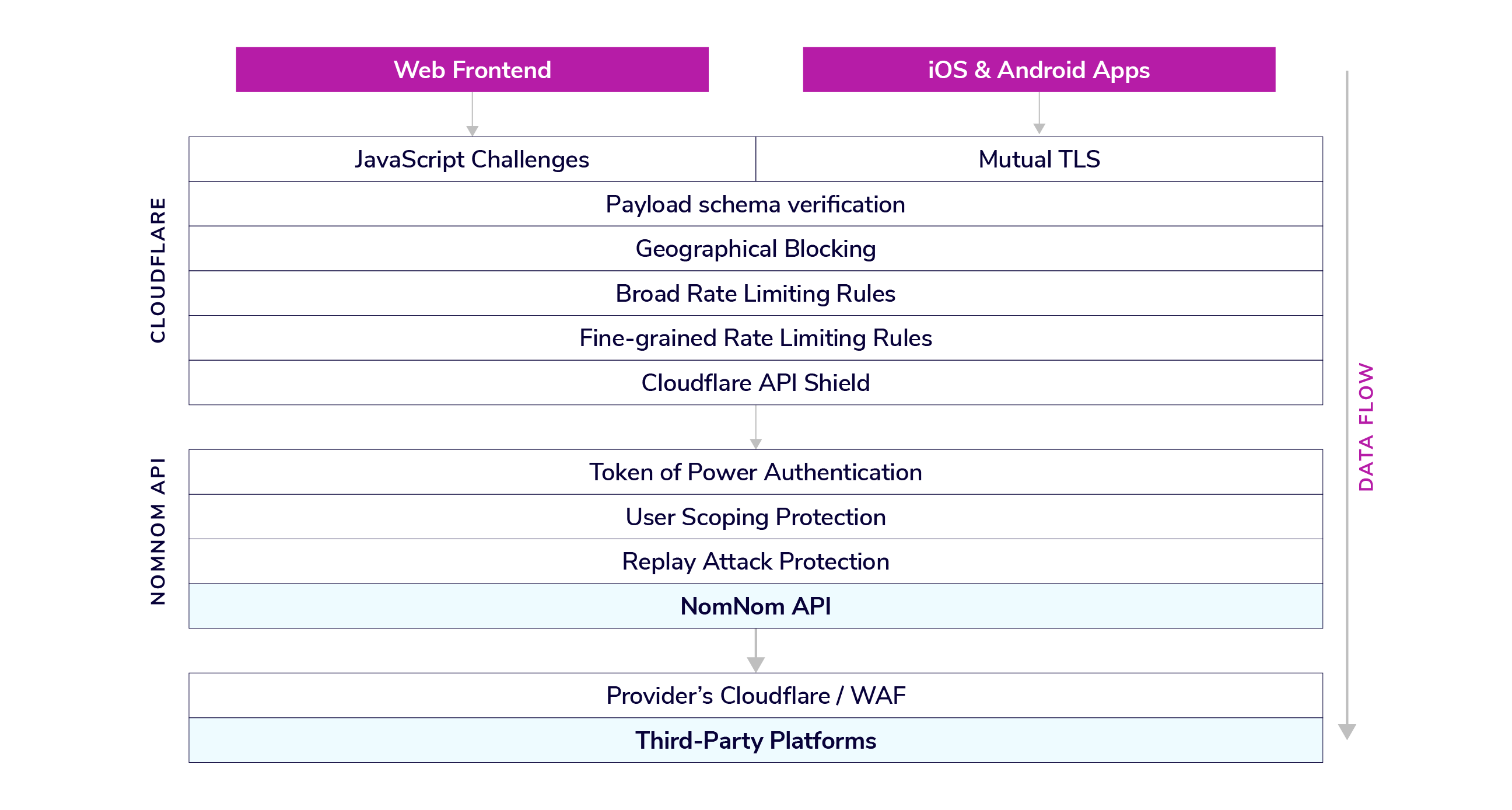
On top of these measures, most of our third-party integrations employ their own edge security layer (like Cloudflare), and our security team coordinates with these partners to ensure we are passing all required information to enable their WAF to do its job as well. It is crucial to work with our partners' security teams to ensure that legitimate traffic is processed and attacks are stopped.
Security by the Numbers
To give you an idea of the scale of cyberattack defense NomNom provides, here are a few statistics from the first half of 2024:
- For a selection of NomNom brands, about 23.81 billion requests passed through the Cloudflare WAF layer
- Among those requests, about 882 million login requests were deemed to be suspicious and were challenged or blocked before they were allowed to be processed
- About 198 million different discreet threats were identified and addressed by Cloudflare
On average, approximately 1-2% of the total traffic that the WAF processes is considered suspicious and is either challenged or blocked. From there, it is prevented from accessing the NomNom servers or the third-party partners integrated with NomNom, which ensures customer data and transactions remain secure.
Without the WAF, or if the security layers were not effective deterrents, the number of attacks would likely skyrocket, since the more successful the attacks, the more frequently bad actors will target a site before it is locked down.
Continuing to Evolve Security
Security is ever changing and requires constant vigilance. It’s all about layers of protection; even as we add a layer, it is inevitable that bad actors will learn and adjust to those layers. Knowing this landscape, we are always evolving our security layers to ensure we remain effective in protecting our clients and their customers.
One example of this evolution is our utilization of Cloudflare's Managed Challenge capability across all platforms, rather than just web and web-based hybrid iOS and Android applications. Historically, it has been difficult to apply a Managed Challenge to natively-built iOS and Android apps, but Cloudflare recently introduced their Turnstile product that not only enhances the types of challenges that can be issued, but also provides a way to show them on natively-built apps. Our NomNom security and Core teams jumped into action to prototype and test this new mechanism, and we will be including support for it in an upcoming Core Package update for NomNom that our clients can get the benefit of right away.
We’re also introducing a brand-new feature to give users more control over their own security, and addressing a major gap that loyalty and online ordering platforms have had for some time.
Introducing The NomNom MFA Service
In the next few months, the NomNom team will be releasing an MFA Service that can be layered on top of any identity provider that does not support MFA challenges. These challenges can be made required when customers login or sign up, or it can be dynamically applied at points in the experience where fraud is likely to occur, with the primary use case being applying an MFA challenge when checking out using a saved credit card on an account. This means that even if a customer's account is compromised by a credential stuffing attack, it couldn’t be used to place orders or change the account password, which effectively eliminates the value of an attacker spending resources performing a credential stuffing attack in the first place.
Since NomNom is meant to accelerate work but also give brands the ability to infinitely customize the experience, we built the MFA service to fit that model as well. At the core of the MFA feature is a proprietary service that issues and verifies MFA codes through email, SMS, and eventually even app-based authenticators. This service was built to be generic so it can be leveraged in a variety of ways by our brands that are on NomNom. The NomNom team is incredibly excited to deliver this feature that will address a critical security gap and make our clients’ deployments and their customers’ accounts safer than they’ve ever been before.
The Future: Moving Away From Passwords
At Bounteous x Accolite, we continuously monitor trends in customer experiences and security to enhance our solutions. One exciting trend we see emerging for restaurants is the shift to passwordless login systems. Instead of traditional email and password logins, customers enter their email or phone number and receive a magic link or one-time password (OTP) to their device. Clicking the link or entering the OTP logs them in. This method leverages the stronger security of SMS and email accounts, which are often protected by multi-factor authentication (MFA), providing a more secure login experience.
The concept of passwordless login is relatively new, and we anticipate needing an onboarding process to help customers understand its benefits. Many users assume passwords are more secure, so we will work with our brands to educate customers and smoothly transition them to this more secure login method.
If you would like to see a passwordless flow in action, take a look at the Dutch Bros app (iOS, Android), which Bounteous originally built for the brand. The passwordless login flow we developed together is incredibly clean and intuitive, and it’s a great example of how to implement the passwordless flow well.
As digital transactions become more prevalent in the restaurant and convenience store industries, robust security measures are essential to protect customer information. By staying ahead of emerging threats and adopting innovative solutions like passwordless login systems, we aim to provide our clients and their customers with the highest level of security and peace of mind. Together, we can create safer digital experiences and build trust in the digital age.